Hi Folks,
as a continuation from the previous post, we're going to take a look at ZyXEL LTE3301-M209.
[!] Togheter with Zyxel PSIRT, we decided not to reveal the credentials. In addition, due to the impact it may have, some steps are skipped.
The telnet "backdoor" is not limited to the D-Link DWR-921 and seems to be present on the ZyXEL LTE3301-M209 as well.
FW version: 20191202 V1.00(ABLG.4)C0
MD5:8A2C093431456BFDC8D3DD0403EC1632
Same speech, let's go straight to the commander elf, as seen in the previous post:
 |
| commander elf from ZyXEL fw |
|
|
|
|
|
same amit* functions, same producer means same backdoor?! Not really.
In the first case, since having the D-Link phisically, I had a chance by rdcsman tool to read the password from the device. I now have no phisical access to the device and I have to dig the password out from the config.
The firmware is basically a merge of 3 sections, the LZMA section is the kernel, at 0x148CD6 the root-fs and at 0x90BD36 the www content.
Inside the last Squashfs there is a [censored] file which is contains at 0x10 the Zlib magic bytes.
To unpack the file you can use openssl or zlib-flate in unix or alternatively transform the zlib into a gzip file in windows and make it readable by 7zip.
Going brutally down by strings there is no one good telnet password however....
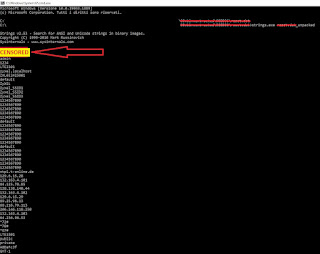 |
WebUI Credentials
|
An interesting sequence appeared: username / WebUIFakePassword .By looking at telnet creds I've actually landed on something which looks like a backdoor in the webUI!!
[few steps are hidden]
Same as before and unpack the config.dat is going to contain the telnet login password: "TelnetFakePassword"
Let's put things togheter:
On ZyXEL LTE3301 we have two ways to own the device:
1) webUI credentials --> username / WebUIFakePassword
2) telnet credentials --> root / TelnetFakePassword
An additional note: from what i see, telnet password is not included in the reset.dat so, if rewritten, it may remain permanently modified regardless of reset.
Upgrade your device with the latest firmware ASAP!
History:
12 Sep 2022: Vulnerability reported to ZyXEL
13 Sep 2022: ZyXEL asks for detail in order to replicate the vulnerability.
13 Sep 2022: Details sent to ZyXEL.
14 Sep 2022: ZyXEL confirm that the issues only affect the LTE3301-M209 model. They're working to the vendor to fix it. They asks to keep information confidential until patch has released.
17 Sep 2022: Waiting for the patch.
19 Oct 2022: The issue is now tracked by CVE-2022-40602
22 Nov 2022: ZyXEL's security bullettin published. Firmware fix has been released.
24 Dec 2022 Hopefully users has now updated their own devices, It's time to make my blog post public.
Cheers!
RE-Solver
























